When scientists start a new project, they have a lot of plates spinning in the air. The ACCESS Operations team doesn’t want researchers to worry about security on top of everything else, so they’ve been working to make sure using ACCESS is a smooth process and that researchers won’t even notice the team’s efforts to keep data secure and safe.
Derek Simmel, co-principal investigator (co-PI) and cybersecurity lead for ACCESS Operations, recently presented in a webinar through Trusted CI on the progress that the ACCESS Operations cybersecurity team has made toward meeting their goals. Operations stated mission is to serve as a source of innovation and support across the NSF-funded cyberinfrastructure ecosystem while also seeking to evolve, advance and expand that ecosystem across the areas of cyberinfrastructure operations, resource integration, data and networking, cybersecurity and the cyberinfrastructure professional workforce. Their goals support this mission in many ways through providing operational support, delivering core services, seeking novel and innovative ways to expand and broaden participation in the ACCESS ecosystem and contributing to the cyberinfrastructure workforce through training and engagement.
Our goal is to provide a stable network, to lead in cybersecurity, and to provide a reliable ecosystem so that everybody who needs to get to the HPC resources that are allocated can do so as easily, securely and efficiently as possible.
Derek Simmel, co-PI and cybersecurity lead, ACCESS CONECT
To further advance cybersecurity within ACCESS, the cybersecurity team has adopted the Trusted CI Framework to structure its program. Speaking about this framework, Simmel explains that by adopting the Trusted CI Framework, his team seeks to lead by example. “This is not a low standard by any means,” he says. “As those who have adopted the framework understand, this is a standard above which one must comply to be successful, so it sets a good bar, and it’s very comprehensive. We’re very glad to have it available to pin all the needs that we have in excellence for our cybersecurity program.”
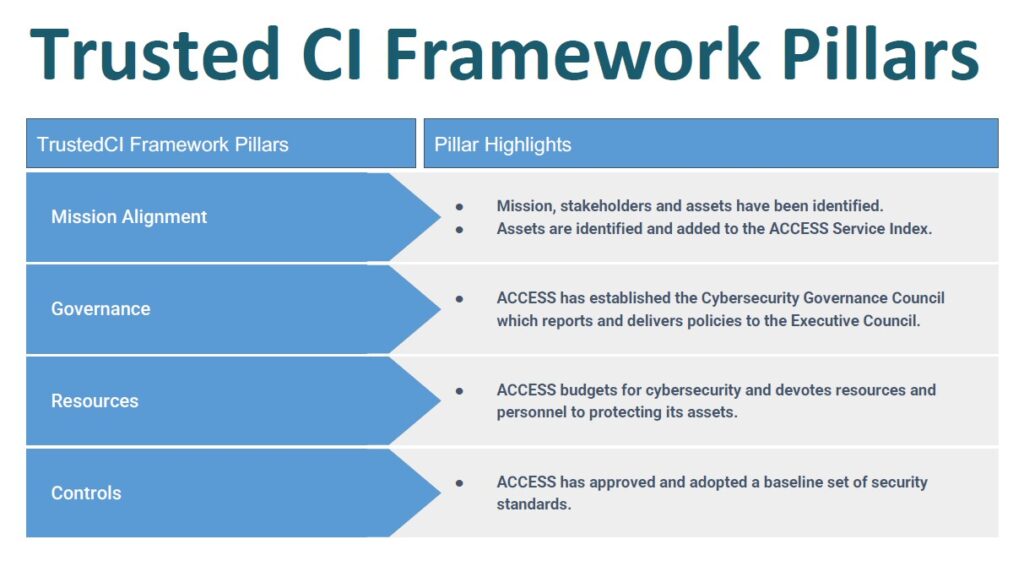
The cybersecurity team has had enormous success since the start of ACCESS. One example comes from the Identity and ACCESS Management working group led by Jim Basney. His team migrated more than 100,000 entities from XSEDE into ACCESS during the transition. The process went so smoothly that Simmel called it a great achievement. “[Basney’s team’s] primary goals were to make sure that in the transition between XSEDE and ACCESS, we had a consistent identity and access management system and that it went as smoothly as possible with as little disruption to research activities.” Simmel went on to detail the work that Basney’s team accomplished.
“Basney’s group went through an enormous amount of effort, especially in the early months, through several rapid rounds of design, review, revision, re-review and prototype development together with ACCESS partners before they were able to build what has been a remarkably successful, COmanage-based identity registration system. Remarkable, not because we’re surprised that it works. We’re just really happy that it works as well as it does…To our knowledge, this is the largest known single ingest of identities into a COmanage registry to date.”
Simmel’s team knows this is just the start. They’ve learned both from their accomplishments and the hurdles they encountered along the way. “Relationship building really is trust building,” Simmel says. “You can’t get anything done in cybersecurity if you don’t have buy-in. And the only way to do that is to go out and encourage participation, to negotiate. Help people understand that you’re working for them and not just imposing rules on them.” Simmel adds that it’s also important to remember not to reinvent the wheel. “Don’t invent your own infrastructure if you don’t have to. Use the lessons and the good work of others to build your systems. That has really worked for us.”
Operations: Year 1 Accomplishments
- Developed core Cybersecurity Policies for ACCESS
- Established the ACCESS Cybersecurity Governance Council
- Built and deployed a comprehensive identity and access management (IAM) infrastructure
- COmanage registration system and CILogon authentication plus DUO multi-factor authentication engineered for 100K+ users
- Deployed active vulnerability scanning and management
- Convened ACCESS Incident Response and Trust Group
On what comes next for his team, Simmel spoke about several future goals. “We want to add configuration management tools support for the system security baseline,” he says. “So, not just telling you what you need to do, but if we can, for example, provide Ansible scripts or Puppet configurations that you can just absorb into your own local management system, and it will check the baseline security boxes for you, we’d like to do that.”
As he finished his presentation, Simmel spoke on one of the areas he hopes his team can improve over the next year. “One area that I’d really like to put more effort into is the training and outreach efforts, use the STEP program and also work with partners such as Trusted-CI to deliver cybersecurity awareness and training to the R&E [Research and Education] community.”
If you’d like to see the full presentation, you can find it here on the Trusted CI webinars page, where you can also find other webinars specializing in cybersecurity topics chosen specifically for the NSF science community.


